Pseudo-technical descriptions of the science and technology in Zero-K.
Technobabble, ZK edition! Just for fun, don't take too seriously. Work in progress, feel free to add/correct.
Sensor equipment and Line of Sight
All units on the battlefield employ a combination of active and passive stealth technology. These include electromagnetic radiation propagation controlling surfaces, passive radar profile minimization, Cyber warfare modules, IR shielding and intelligently deployed active jamming.
The practical upshot of this is that units have a limited visual range, despite having a clear line of sight to target. Because the stealth technology is fairly standardized across most units, the range that a unit can detect the enemy depends on the sophistication of the sensor hardware and software installed on that unit.
Plasma
The plasma cannon uses arc-generated thermal plasma that is injected into a ceramic/fullerene composite shell just prior to firing. The solid shell prevents the plasma from dispersing before it reaches its target, and gives the projectile good ballistic characteristics. Because of the extreme temperature involved, the shell glows much like a “naked†plasmoid would.
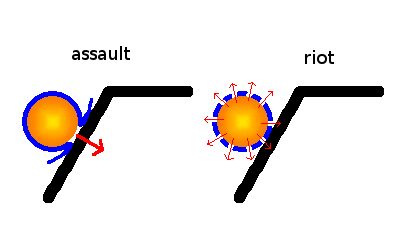
The containment shells are rated to last from one to ten seconds (depending on the weapon design) before disintegrating under the stress and releasing the contained plasma. “Assaultâ€-type shells are designed to release their plasma forward when striking a solid object, like a shaped-charge. The walls of a “Riotâ€-type shell are roughly even all around, so release their plasma explosively in all directions.
Gauss
The Gauss cannon, also known as the Coilgun or Mass Driver, uses a magnetic acceleration ladder to propel solid projectiles at speeds exceeding almost 10,000 meters per second. The sheer kinetic force exerted by these weapons allows it to pierce straight through most solid matter, including most variations of modern composite armor.
Lightning
Whilst nowhere near the power of natural lightning, similar streams of electrons have been effectively harnessed for use as a potent weapon. The firing sequence comes in two parts — firstly, the gun system will paint a proton 'patch' on the target. Milliseconds later, a high-voltage pulse is released from the weapon, which seeks out the charge differential and annihilates the target. Such devices have the potential to inflict horrific superficial damage, as well as overloading most units' electrical buffers and stunning them briefly.
Cloaking
“Cloaking†is the colloquial name for the Electromagnetic Active Camouflage, often abbreviated to “emac†by technical personnel (although it is almost never referred to by that name by field commanders). It makes a unit transparent to all forms of EM radiation striking its surface by making photons "flow" around it, as well as preventing IR radiation from leaving the unit’s body. The unit is thus rendered nearly undetectable. Small gaps in the field are left for the sensors, allowing the unit to see as normal.
Careful pumping of air through a heat discharger and venting it to the atmosphere while still only warm prevents the unit from overheating without giving away its position. However, an enemy unit sufficiently close will still detect the emissions, revealing the cloaked units. Additionally, firing weapons will either overload the cooling system or else allow the enemy to trace the weapons fire back to its origin. The exception is the Sharpshooter sniper bot, which has a very energy-efficient weapon and can dump waste heat from its gun into an insulated heatsink which can be discarded and replaced as necessary.
Cloaking cannot be used as a defense against weapons-grade lasers, which will overwhelm it easily. Additionally, kinetic impacts and energy weapons will disrupt the cloaking field, briefly revealing the targeted units. Cloaking also has no effect on sonar detection systems.
Cloaking v2
“Cloaking†is the colloquial name given to units employing a range of specialized stealth technologies and design features, especially the Electromagnetic Active Camouflage, called “EMAC†by the ancient humans that invented it. These include circuitry designed to operate at extremely low temperatures, high efficiency generators and motors to reduce the heat output combined with extreme insulation and exterior cooling systems to mask their heat signature. Rather than just relying on the passive EMR propagation controlling surfaces, the EMAC device generates a light manipulation field which creates a more perfect invisibility. The field is configured to allow rotating narrow bands of EMR in, but not back out of the field to allow the cloaking unit to see through it's own cloak. Due to the sophistication of the sensors required, any units under a cloaking units EMAC field are relayed sensor data from the cloaking unit. Communications are likewise piped in out through a rotating narrow bandwidth hole in the cloaking field.
These technologies render the units invisible at much shorter ranges than the standard stealth technology. However at extremely close range enemy units can detect the slight heat profile, minor EMR distortion, magnetic distortions, and particular residue produced by the external cooling system, allowing an enemy to triangulate the cloaked unit and even identify it's design.
In battle, high energy weapons create localized disruptions in the cloak field. This means that any unit within a cloak field that is hit with a weapon or fires a weapon will become visible to the enemy. The exception is the Sniper, which employs a delicate, highly specialized weapon designed not to disrupt it's own cloak field.
Lightning gun Cyber warfare system OR Dominatrix weapon (?)
The weapon system is designed to take advantage of the tight control commanders have over their units.
The gun portion of the weapon system delivers a high energy pulse designed to jam and overwhelm the targets communication system. To prevent the target from simply going into full autonomous mode, The pulse is tailored to specifically leave one standard communication frequency open. The lightning gun weapon system then transmits a sophisticated cyber warfare attack on that frequency. It mimics the command signals from the unit's commander - which the comm system is programmed never to ignore - to install a new sequence in the comm boot-up system. Before the anti-virus can detect this, the lightning gun delivers another high power pulse to over-load the communication system into shutting down. As it re-boots, a portion of the virus goes un-detected in the communication system bios. This all happens in a fraction of a second.
The more advanced the units communication system, the more attacks are required before the virus is complete. Once the virus has finished assembling itself, it repeatedly initiates the commander over-ride system re-boot command - one of the few commands that a commander can issue that doesn't require confirmation from the units higher level Turing system (designed to allow the commander to re-set machines which had developed errors, or who had evolved a conscience). The target's anti-virus then has brief micro-second intervals between shut downs to clear out the virus from the communication system.